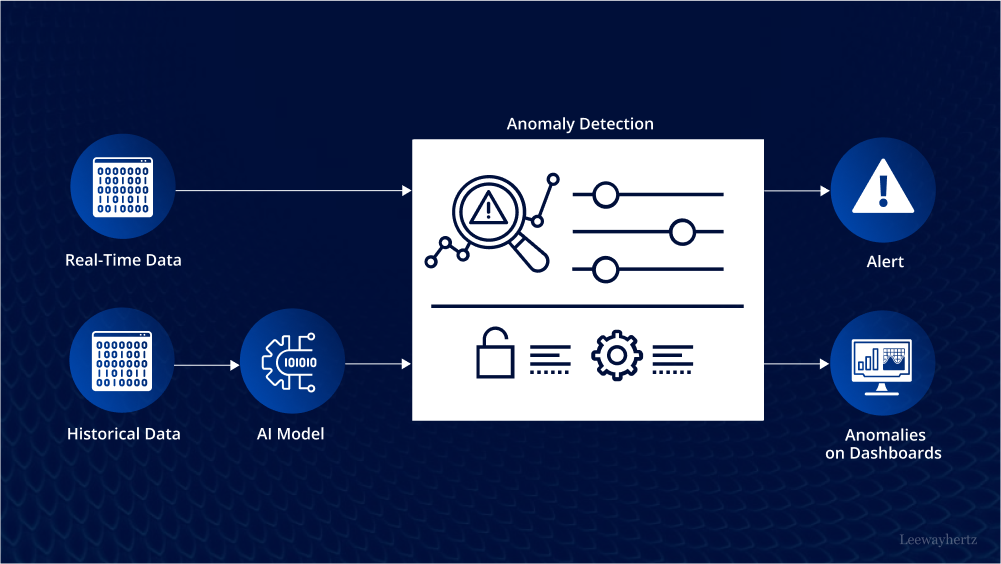
AI in anomaly detection: Uncovering hidden threats in data in real time
- What are anomalies?
- What is anomaly detection in AI?
- Use cases of AI in anomaly detection
- Why do you need machine learning for anomaly detection?
- What are the different anomaly detection methods?
- Machine learning algorithms for anomaly detection
- Use cases of AI in anomaly detection
- Intrusion detection in cybersecurity
- Fraud detection and operational optimization
- Health monitoring, healthcare quality and fraud prevention
- Defect detection using anomaly detection system
- Application performance management
- Ensuring product quality
- Enhancing user experience
- Identifying inefficient equipment and tools in manufacturing
- Mitigating risks and enhancing security in IT and telecom
- How LeewayHertz’s generative AI platform helps in anomaly detection in diverse business environments?
What are anomalies?
Anomalies, in the context of data analysis and processing, refer to peculiar data points that deviate significantly from a dataset’s expected or normal behavior. These deviations, whether large or small, can appear as a sudden spike or dip in activity, an error in the text, or an unusual change in temperature. But what makes these anomalies significant? And why is understanding them vital in various fields like finance, healthcare, and software engineering? An anomaly is like a red flag in the data stream, signaling something that needs attention. They are not mere statistical quirks but can be indicative of underlying issues or opportunities. Let’s explore the various facets of anomalies:- Outliers: These are sporadic, non-systematic anomalies that do not conform to the general pattern in data. They may result from data preprocessing errors, noise, fraud, or even cyber-attacks. An outlier might signify fraudulent transactions in financial contexts, as seen when large, atypical sums of money are spent quickly.
- Change in events: Representing a sudden or systematic shift from previous behavior, these anomalies can signify critical changes that demand immediate attention. A sudden drop or increase in temperature in industrial machinery could indicate a malfunction or impending failure.
- Drifts: Unlike sudden changes, drifts are slow, unidirectional, long-term variations in the data. They might signal underlying trends or shifts in behavior that could have long-term impacts.
What is anomaly detection in AI?
Anomaly detection, also known as outlier detection, is a vital aspect of data science that centers on identifying unusual patterns that do not conform to expected behavior. An anomaly detection system works by assessing and comparing data points within a dataset, singling out those that stand out from the normal pattern. The significance of AI in anomaly detection isn’t merely about finding statistical quirks; it’s about uncovering valuable insights, underlying problems, or opportunities that might otherwise go unnoticed.Techniques and approaches
Different techniques and algorithms can be employed in anomaly detection, ranging from statistical methods to machine learning algorithms. The choice of method often depends on the nature of the data and the specific use case.- Statistical methods: Using statistical tests and probability distributions to model normal behavior, anything that deviates significantly from this model can be flagged as an anomaly.
- Machine learning algorithms: We can detect patterns and deviations utilizing supervised or unsupervised learning techniques. Unsupervised learning is particularly powerful in cases where labeled data is scarce, and the system must learn what constitutes an anomaly on its own.
- Hybrid approaches: Combining various methods to create a more robust detection system capable of handling complex scenarios and adapting to evolving patterns.
Use cases of AI in anomaly detection
Cybersecurity
- Network traffic monitoring: AI-powered Intrusion Detection Systems (IDS) continuously monitor network traffic, analyzing packet headers, payload data, and communication patterns to detect anomalies or suspicious activities that may indicate unauthorized access, malware infections, or cyber-attacks.
- Signature-based detection: AI employs signature-based detection techniques to compare network traffic against known patterns or signatures of known cyber threats, including viruses, worms, and malware. AI enhances this process by rapidly identifying and updating signatures based on new threat intelligence.
- Behavioral analysis: AI can analyze network behaviors over time to detect subtle changes or trends indicating emerging threats or sophisticated cyber attacks. These systems can detect previously unseen attack patterns by learning from historical data and real-time observations.
- Real-time alerting and response: AI-powered IDS provide cybersecurity teams with real-time alerts upon detecting potential intrusions or security breaches. These alerts include detailed information about the nature of the threat, affected systems, and recommended mitigation strategies, enabling swift response and remediation.
Finance
- Transaction monitoring: Machine learning-based fraud detection systems analyze transaction data in real-time to detect anomalies such as unusual spending patterns, high-value transfers, or transactions from suspicious locations.
- Identity verification: AI-powered systems verify the identity of individuals applying for financial services, such as loans or credit cards, by analyzing biometric data, document scans, and other authentication methods to detect fraudulent identity theft attempts.
- Account monitoring: Fraud detection systems continuously monitor account activities, such as login attempts, fund transfers, or changes in account settings, to detect anomalies indicative of account takeover, unauthorized access, or fraudulent activities.
- Behavioral analysis: AI algorithms analyze customer behavior patterns, such as browsing habits, transaction history, or spending preferences, to detect anomalies or deviations from normal behavior that may indicate fraudulent activities or suspicious behavior.
- Fraudulent application detection: Machine learning models scrutinize loan applications, insurance claims, or credit card applications to detect inconsistencies, discrepancies, or fraudulent information, such as fake documents, forged signatures, or misrepresented financial details.
Manufacturing
- Defect recognition: AI-driven anomaly detection systems are trained on large datasets of defective and non-defective parts to learn the characteristics of different defects. Using techniques such as convolutional neural networks (CNNs), these systems can accurately identify subtle defects such as cracks, scratches, dents, or irregularities in shape, size, or color.
- Real-time monitoring: Anomaly detection systems continuously monitor the production process in real-time, scanning each component through the inspection. Any deviations from the expected specifications or quality standards trigger immediate alerts, allowing operators to take corrective actions promptly and prevent the production of defective parts.
- Integration with machinery: Anomaly detection systems can be integrated directly into manufacturing machinery or production lines to monitor internal systems and components. For example, machine sensors measure various parameters such as temperature, pressure, vibration, or energy consumption. AI algorithms analyze these data streams to detect anomalies indicating potential malfunctions or maintenance issues.
- Predictive maintenance: By detecting anomalies in machinery and equipment, anomaly detection systems enable predictive maintenance strategies. By pinpointing potential problems before they evolve into expensive breakdowns, manufacturers can enhance their operational efficiency and extend the lifespan of their equipment. This proactive approach allows manufacturers to schedule maintenance tasks more efficiently, reducing downtime and avoiding costly disruptions in production. Additionally, by addressing issues preemptively, manufacturers can optimize the performance of their equipment, leading to improved reliability and longevity.
Telecommunications
- Network security: Anomaly detection systems monitors network traffic, call records, and signaling data to detect suspicious activities, unauthorized access attempts, or cyber-attacks targeting telecommunication networks. By analyzing anomalies such as unusual call patterns, unexpected data transmissions, or abnormal network behaviors, telecom providers can identify and mitigate security threats to protect against network breaches and data breaches.
- Fraud prevention: Anomaly detection systems monitor billing records, call detail records (CDRs), and subscriber activities to detect fraudulent activities such as subscription fraud, call spoofing, or toll fraud. By analyzing anomalies such as sudden spikes in call volumes, unusual calling patterns, or discrepancies in billing data, telecom providers can proactively prevent revenue losses, safeguard customer accounts, and uphold the integrity of their billing systems.
- Quality of Service (QoS) monitoring: Anomaly detection helps monitor network performance metrics such as latency, packet loss, and jitter to ensure optimal quality of service for telecommunication services. By detecting anomalies in QoS metrics, telecom providers can identify network congestion, service degradation, or performance bottlenecks, enabling timely interventions to maintain high-quality service delivery and customer satisfaction.
- Capacity planning: Anomaly detection systems analyze network traffic patterns, subscriber growth trends, and resource utilization data to forecast future demand and plan capacity expansion. By identifying anomalies such as unexpected traffic surges, capacity bottlenecks, or resource constraints, telecom providers can optimize network infrastructure investments, improve resource allocation, and ensure scalability to meet growing demands.
- Network fault detection: Anomaly detection monitors network equipment, such as routers, switches, and transmission lines, for signs of malfunctions, hardware failures, or service disruptions. By analyzing anomalies in device performance metrics, error logs, or network alarms, telecom providers can detect and address network faults more quickly, minimizing downtime and ensuring customer service availability.
Healthcare
- Remote patient monitoring: Anomaly detection systems in healthcare continuously monitor patient data collected from wearable devices, sensors, or electronic health records. They identify anomalies in vital signs, activity levels, or medication adherence, alerting healthcare providers to potential health issues or changes in a patient’s condition.
- Early disease detection: AI-driven anomaly detection helps in the early detection of diseases by analyzing patterns in medical data such as genetic markers, biomarkers, or diagnostic tests. It flags anomalies that may indicate the onset of diseases such as cancer, diabetes, or cardiovascular conditions, enabling timely interventions and preventive measures.
- Chronic disease management: Anomaly detection systems track longitudinal patient data to detect deviations from baseline health parameters in individuals with chronic conditions such as hypertension, diabetes, or asthma. They alert patients and caregivers to potential exacerbations or complications, facilitating proactive management and reducing hospitalizations.
- Clinical decision support: Anomaly detection systems assist healthcare providers in clinical decision-making by identifying deviations from evidence-based guidelines, best practices, or quality metrics. They flag outliers in treatment outcomes, medication adherence, or diagnostic accuracy, enabling clinicians to optimize care delivery and improve patient outcomes.
- Patient safety monitoring: AI-driven anomaly detection enhances patient safety by identifying adverse events, medical errors, or near misses in healthcare settings. It analyzes incident reports, medication errors, or adverse drug reactions to identify patterns indicative of systemic issues or areas for improvement in patient safety protocols.
- Quality improvement initiatives: Anomaly detection in healthcare supports quality improvement initiatives by analyzing performance metrics, patient satisfaction scores, or clinical outcomes data. It identifies variations in care delivery, resource utilization, or adherence to clinical protocols, enabling healthcare organizations to implement targeted interventions and drive continuous quality improvement.
- Claims fraud detection: Anomaly detection systems analyze healthcare claims data to identify patterns indicative of fraudulent activities, such as upcoding, unbundling, or billing for medically unnecessary services. They flag billing codes, service utilization, or provider behavior anomalies, enabling payers to investigate and prevent fraudulent claims.
- Behavior detection: Anomaly detection systems monitor electronic health records, prescription data, or billing records for unusual activities that may indicate identity theft, medical identity fraud, or prescription drug abuse. They flag anomalies such as unauthorized access to patient records, unusual prescribing patterns, or discrepancies in patient demographics, enabling healthcare organizations to prevent fraud and protect patient information.
Retail
- Transaction security: Anomaly detection systems monitor retail transaction data, including payment card transactions, online purchases, and point-of-sale transactions, to detect fraudulent activities such as credit card fraud, identity theft, or payment fraud. By analyzing unusual spending patterns, high-risk transactions, or suspicious payment activities, retailers can identify and prevent fraudulent transactions, protect customer financial information, and maintain trust in their payment systems.
- Inventory management: Anomaly detection helps retailers optimize inventory management by monitoring sales data, stock levels, and supply chain activities to detect anomalies such as stockouts, overstocking, or inventory shrinkage. By identifying anomalies in inventory turnover rates, order fulfillment times, or demand forecasting accuracy, retailers can improve inventory planning, reduce holding costs, and minimize stockouts, ensuring timely product availability and customer satisfaction.
- Customer behavior analysis: Anomaly detection systems analyze customer behavior data, including browsing patterns, purchase histories, and loyalty program activities, to detect anomalies such as unusual shopping behaviors, account takeovers, or fraudulent activities. By detecting sudden changes in shopping preferences, account login attempts from new locations, or unusual redemption patterns, retailers can identify potential security threats, protect customer accounts, and personalize marketing strategies to enhance customer engagement and loyalty.
- Supply chain security: Anomaly detection monitors supply chain data, including supplier performance, shipping logistics, and inventory movements, to detect anomalies such as delivery delays, shipment discrepancies, or supply chain disruptions. By analyzing anomalies in supply chain metrics, retailers can identify potential risks, mitigate disruptions, and ensure the reliability and security of their supply chain operations, thereby maintaining seamless product availability and fulfilling customer demand.
- Loss prevention: Anomaly detection systems help retailers prevent losses due to theft, shrinkage, or fraudulent activities by monitoring security camera footage, employee access logs, and transaction records to detect anomalies such as suspicious behaviors, unauthorized access, or unusual activities. By analyzing anomalies such as unusual movements in in-store traffic, discrepancies in inventory counts, or patterns indicative of internal theft, retailers can enhance security measures, deter criminal activities, and safeguard assets and profits.
Launch your project with LeewayHertz!
Achieve operational efficiency and security with our expert-built anomaly detection systems that help you uncover hidden threats in data.
Why do you need machine learning for anomaly detection?
Anomaly detection is a sophisticated process that identifies unusual patterns deviating from expected behavior. As businesses grow and their operations become increasingly complex, the necessity for machine learning in anomaly detection becomes apparent. Let’s explore the reasons behind this need:
Handling vast amounts of data
Modern organizations manage enormous quantities of diverse data such as transactions, text, images, and videos. Manual inspection of this massive data set would be time-consuming, resource-intensive, and practically unfeasible. The magnitude and rapid generation of data make it impossible to derive valuable insights without automated assistance.
Dealing with unstructured data
A significant portion of the data encountered in businesses is unstructured. This means it is not organized in a predefined manner suitable for analysis. Examples include business documents, emails, and images. The inherent complexity of unstructured data requires specialized tools capable of understanding and processing it.
Utilizing machine learning techniques
Machine learning has emerged as a vital solution in this scenario. ML techniques are adept at handling large data sets and excel in processing diverse data types. Different algorithms can be tailored or combined to fit the specific problem at hand, rendering them versatile and effective.
Real-time analysis and resource efficiency
Machine learning allows for both post-factum and real-time anomaly detection. This real-time capability is particularly essential in areas like fraud detection and cybersecurity, where timely intervention is critical. Automating this process through ML significantly conserves human resources and enhances efficiency.
Improved security and robustness
By employing ML algorithms, businesses can fortify their systems against potential threats and weaknesses. Machine learning’s predictive and analytical capabilities contribute to a more secure and robust operational environment, identifying vulnerabilities before they escalate into significant issues.
Machine learning’s role in anomaly detection is not just a trend but a strategic necessity. The volume, velocity, and complexity of data in modern businesses demand sophisticated tools capable of processing and interpreting it effectively. Machine learning fulfills this need, offering scalability, adaptability, and real-time capabilities that traditional methods cannot match. Its application in anomaly detection signifies a profound shift towards intelligent, responsive, and resilient systems that align with contemporary business requirements.
What are the different anomaly detection methods?
Anomaly detection is a critical aspect of data analysis, particularly in complex systems where identifying abnormal patterns can have significant implications. Several methods are employed to detect anomalies, each with unique features and applications. Here’s a non-repetitive and detailed look at the different types of anomaly detection methods:
Supervised anomaly detection
- Definition and usage: This method requires a labeled training dataset, segregating items into normal and abnormal categories. The model identifies patterns from these examples to detect new, unseen data anomalies.
- Characteristics:
- Training dataset importance: Quality and labeling of the training dataset are crucial.
- Manual effort required: Collecting and labeling examples necessitate substantial manual work.
- Not ideal for sparse anomalies: This method may not be optimal in real-world applications with rare anomaly samples.
Launch your project with LeewayHertz!
Achieve operational efficiency and security with our expert-built anomaly detection systems that help you uncover hidden threats in data.
Unsupervised anomaly detection
- Definition and usage: A prevalent type of anomaly detection, unsupervised methods like Artificial Neural Networks (ANNs) require no manual labeling. They can detect anomalies in unlabeled data and apply learned patterns to new information.
- Characteristics:
- Less manual work: Reduction in manual labor for pre-processing.
- Complexity: High level of intricacy.
- Applicability: Particularly valuable for unpredictable real-life data, such as self-driving cars encountering novel road situations.
- Challenges:
- Black box architecture: Understanding how neural networks label events as anomalies can be obscure.
- Less trustworthy: Unlike supervised techniques, unsupervised methods can be unreliable as they may learn incorrect rules.
Semi-supervised anomaly detection
- Definition and usage: This approach blends the features of supervised and unsupervised methods, utilizing unsupervised learning to handle unstructured data and human oversight to guide pattern learning.
- Characteristics:
- Combines best of both worlds: Automation in feature learning coupled with human monitoring and control.
- Accuracy: Generally provides more precise predictions by merging automated detection with human intuition and expertise.
Anomaly detection methods with machine learning offer various tools to address different challenges and requirements. Supervised methods bring precision but require extensive manual labor, while unsupervised methods offer flexibility but might lack reliability. Semi-supervised methods attempt to bridge these gaps by amalgamating the strengths of both approaches. The choice of method depends on the specific scenario, data characteristics, and the balance between automation and human oversight.
Machine learning algorithms for anomaly detection
Several machine learning algorithms are used for anomaly detection, which varies based on the dataset size and the nature of the problem. These include:
- Local Outlier Factor (LOF): This algorithm detects anomalies by examining the local density of data points. LOF compares a data point’s density with its neighboring points’ density. If the data point has a lower density than its neighbors, it’s considered an outlier.
- K-Nearest Neighbors (kNN): kNN is a supervised machine learning algorithm typically used for classification. For anomaly detection, it operates as an unsupervised algorithm. A machine learning expert defines the range of normal and abnormal values, and kNN classifies these ranges without undergoing traditional learning. It’s advantageous for anomaly detection as it works well on small and large datasets and allows easy visualization of data points.
- Support Vector Machines (SVM): SVM, a supervised classification algorithm, divides data points into classes using hyperplanes in multi-dimensional space. In anomaly detection, SVMs are also applied to single-class problems, where the model is trained to recognize the ‘norm’ and assess whether unfamiliar data belongs to this class or is an anomaly.
- DBSCAN: An unsupervised machine learning algorithm, DBSCAN is based on density principles. It uncovers clusters in large spatial datasets by examining the local density of data points. In anomaly detection, points not belonging to any cluster are classified as -1, making them easy to identify.
- Autoencoders: Autoencoders use artificial neural networks to encode data by compressing it into lower dimensions. Then, these neural networks decode the data to reconstruct the original input. During dimensionality reduction, essential information is retained as the rules have been identified in the compressed data, facilitating outlier detection.
- Bayesian networks: These networks are beneficial for detecting anomalies in high-dimensional data. They are especially useful when the anomalies are subtle and difficult to identify, and visualization on a plot may not yield the desired results.
Use cases of AI in anomaly detection
Intrusion detection in cybersecurity
Intrusion detection is a vital application of AI in the realm of cybersecurity, particularly for companies that handle sensitive data such as confidential information, intellectual property, or the private information of employees and clients. Anomaly detection algorithms are employed in Intrusion Detection Systems (IDS) to continuously monitor network traffic and identify any unusual or suspicious activities.
These AI-powered systems can detect and alert security teams about potentially malicious traffic, including unauthorized access attempts, data breaches, or other cyber threats. Upon detecting such activities, the IDS software sends notifications to the cybersecurity team for immediate investigation and response.
Prominent companies like Cisco Systems and McAfee offer robust intrusion detection software with advanced AI and machine learning capabilities. These tools can autonomously learn from network patterns, adapt to new threats, and provide real-time alerts, thus ensuring a more proactive approach to network security.
The technical sophistication of IDS lies in the application of various machine learning algorithms, including supervised and unsupervised learning, which allow the system to classify normal and abnormal network behaviors. Features such as pattern recognition, clustering, and classification are utilized to distinguish between legitimate and potentially harmful network traffic.
Fraud detection and operational optimization
Machine learning-based fraud detection is an essential application of AI in anomaly detection, especially in the financial sector. It preemptively identifies and prevents illicit attempts to gain money or assets. Banks, credit institutions, and insurance companies extensively use fraud detection software to scrutinize various transactions and applications.
For instance, when evaluating loan applications, banks employ fraud detection systems to validate the authenticity of the submitted documents. These systems cross-reference the information provided in the application with established databases and identify discrepancies. If a discrepancy, such as a non-existent tax number, is detected, the system will automatically flag the application as suspicious and alert the bank’s personnel for further investigation.
In the retail industry, anomaly detection is vital in managing high-value financial transactions and identifying suspicious activities that may indicate fraud, such as identity theft or unauthorized credit card use. By leveraging advanced analytics and machine learning techniques, retailers can monitor transaction data, customer behavior patterns, and other relevant information to detect anomalies or irregularities that deviate from established norms.
For instance, in the case of financial transactions, anomaly detection can help identify unusual purchase patterns, such as sudden spikes in transaction amounts or high-frequency transactions from a single account. These anomalies may indicate potential fraudulent activities, such as unauthorized credit card use or account takeovers.
In addition to transaction data, anomaly detection in retail also involves monitoring customer behavior patterns, such as browsing habits, purchase history, and online interactions. By analyzing these patterns, retailers can detect unusual behavior that may indicate identity theft or other fraudulent activities. For example, if a customer’s account suddenly starts making purchases from a different geographic location or exhibits a significant change in purchase behavior, this could be a red flag for potential fraud.
By detecting these anomalies in real time, retailers can take immediate action to mitigate the risk of fraud, such as blocking suspicious transactions, flagging accounts for further investigation, or implementing additional security measures to protect customer data.
Furthermore, anomaly detection in retail can also be used to optimize inventory management, pricing strategies, and demand forecasting. By identifying unusual patterns in sales data, inventory levels, or customer demand, retailers can make more informed decisions and optimize their operations for maximum efficiency and profitability.
Technically, machine learning plays a pivotal role in enhancing the accuracy and efficiency of fraud detection systems. Various supervised and unsupervised learning algorithms are used to train models on historical fraud data. Over time, these models learn to recognize patterns, correlations, and anomalies that are indicative of fraudulent activities. Advanced techniques such as clustering, classification, and anomaly detection are applied to segregate legitimate transactions from suspicious ones.
Furthermore, AI-powered fraud detection systems can dynamically adapt to new fraud tactics and techniques by continually updating their models based on incoming data. This ensures that the system remains vigilant against both known and emerging threats.
Launch your project with LeewayHertz!
Achieve operational efficiency and security with our expert-built anomaly detection systems that help you uncover hidden threats in data.
Health monitoring, healthcare quality and fraud prevention
Anomaly detection systems play a crucial role in healthcare, aiding medical professionals in diagnostics by identifying unusual patterns in medical images, tests, and other patient data. These systems typically leverage neural networks trained on vast datasets of medical examples, and their proficiency in pattern recognition can sometimes surpass even that of highly experienced doctors.
The technical foundation of these systems relies on deep learning, a subset of machine learning that excels in handling large volumes of data and complex patterns. In the context of healthcare, Convolutional Neural Networks (CNNs) are often used for analyzing medical images such as MRIs or X-rays. These networks are trained on thousands of annotated images, learning to recognize patterns associated with various health conditions.
Once trained, these neural networks can examine new medical images and pinpoint anomalies that could be indicative of potential health issues. By highlighting these areas of concern, anomaly detection systems provide valuable insights that assist doctors in diagnosing and devising appropriate treatment plans. As a result, using AI in health monitoring increases the efficiency and accuracy of medical diagnoses, potentially leading to better patient outcomes.
Besides, anomaly detection plays a crucial role in healthcare management by enhancing the quality of care and preventing significant financial losses. Specifically, it is applied to detect fraudulent claims made by hospitals and on behalf of insurance companies.
By leveraging sophisticated machine learning algorithms and statistical analysis techniques, healthcare organizations can monitor large volumes of claims data to detect irregularities or unusual patterns. These anomalies might include discrepancies in billing codes, inflated charges, duplicate claims, or claims for services not rendered. By identifying these anomalies, healthcare organizations can uncover potential fraudulent activities and take appropriate actions to investigate and address them.
In addition to fraud detection, anomaly detection in healthcare can also be applied to monitor patient data, such as vital signs, lab results, and medical history. By analyzing this data, healthcare organizations can detect unusual patterns or deviations from established norms that may indicate potential health issues or complications. This early detection allows healthcare providers to intervene more quickly and improve the overall quality of care.
Furthermore, anomaly detection in healthcare can also be used to optimize operational efficiency, such as scheduling, resource allocation, and inventory management. Healthcare organizations can make more informed decisions and optimize their operations for maximum efficiency and cost-effectiveness by identifying unusual patterns in patient flow, staff utilization, or medication usage.
Defect detection using anomaly detection systems
Defect detection is a crucial application of AI in manufacturing. Manufacturers who supply clients with machinery or component parts risk significant financial losses in lawsuits if these items have defects. Even a single defective part that does not meet production standards can lead to catastrophic failures, such as a plane crash, with devastating consequences.
Anomaly detection systems utilizing computer vision are highly effective in identifying defects in manufactured parts. These systems can scan thousands of similar components on a production line and detect any anomalies that might indicate a defect. They use advanced image recognition and machine learning algorithms trained on vast datasets of both defective and non-defective parts, enabling them to recognize subtle deviations from the norm.
In addition to detecting defects in manufactured components, anomaly detection systems can also be integrated into the machinery itself to monitor internal systems. These systems can track various parameters, such as engine temperature, fuel levels, etc. By continually monitoring these parameters, the systems can identify any anomalies that may signal potential malfunctions or operational issues.
Technically, the effectiveness of these systems relies on the combination of computer vision and machine learning algorithms. Convolutional neural networks and other image processing techniques are used to analyze images of the manufactured parts and identify any visible defects. Simultaneously, machine learning models are trained on historical data of internal system parameters to recognize patterns and detect deviations from the expected behavior.
Application performance management
The performance of applications directly influences revenue generation and employee productivity. Traditional approaches to application performance monitoring are often reactive, only addressing issues after they have already impacted the organization.
By employing deep learning anomaly detection, organizations can shift from reactive to proactive in managing application performance. Deep learning-based anomaly detection uses machine learning techniques to correlate data with relevant application performance metrics, offering a comprehensive view of business-critical issues. With this information, IT teams can take timely and informed actions to mitigate potential problems before they escalate.
Technically, deep learning anomaly detection involves training machine learning models on vast historical application performance data datasets. These models learn the patterns, trends, and normal behaviors associated with optimal application performance. Once trained, these models continuously monitor incoming performance data, instantly identifying any deviations from the established patterns.
The effectiveness of these systems stems from their ability to correlate and analyze data across multiple application performance metrics automatically. By doing so, they can pinpoint the root cause of performance anomalies, helping IT teams to diagnose and address underlying issues quickly.
Ensuring product quality
Product managers have a responsibility that goes beyond relying on other departments for monitoring and notifications. It’s crucial to ensure the consistent quality and proper functioning of a product from its initial release through every subsequent update and feature addition. With products continually evolving, introducing new versions, A/B tests, features, purchase funnel modifications or customer support changes, abnormal behavior can easily arise. Failure to monitor these product irregularities can result in significant financial loss and damage to the brand’s reputation.
Anomaly detection provides valuable insights for product-based businesses, and here are two prime examples:
- Fintech: Security is of utmost importance for any digital company, but it is even more critical for fintech firms. These companies handle sensitive financial transactions, and clients and business partners expect their transactions to be secure. Anomaly detection helps fintech firms stay ahead of sophisticated attacks, enabling them to proactively identify and address irregularities before they lead to breaches or fraud.
- E-commerce: While developers can manage the technical aspects of monitoring an e-commerce platform, it is also essential to monitor the conversion rates and business funnel. The product manager is responsible for this. Relying solely on fixed points to monitor dynamic funnel ratios can result in missed crucial alerts, particularly in the context of seasonality. Anomaly detection can help product managers identify sudden changes in conversion rates and other important metrics, allowing for timely responses to any issues.
Technically, anomaly detection involves training machine learning models on historical data, enabling these models to learn the patterns and trends associated with normal product behavior. Once trained, these models can continuously monitor incoming data, identifying any deviations from established patterns. Anomaly detection algorithms can effectively correlate data across multiple metrics, helping product managers and stakeholders diagnose and promptly address issues.
Enhancing user experience
Deploying a faulty version of a product, facing a DDoS attack, or implementing an unsuccessful customer service process change can all result in user experience disruptions. Proactively optimizing and enhancing user experiences can significantly improve customer satisfaction in various industries, including:
- Online business: For any online business, seamless operation is crucial. IT teams must swiftly address API issues, load-time problems, server downtime, and other factors that could impact user experience (UX). Anomaly detection provides comprehensive coverage and rapid response times across all platforms, operating systems, and data centers. For example, Wix employs anomaly detection to quickly identify and investigate the root causes of potential problems through a single, unified platform.
Technical Implementation: Anomaly detection in online businesses often involves monitoring various metrics related to website performance, such as API response times, page load times, server uptime, and more. Machine learning models are trained on historical data to learn the patterns and trends associated with optimal website performance. These models can then monitor real-time data and instantly detect any deviations from the established patterns, enabling IT teams to address issues before they impact the user experience. - Gaming: The complexity of gaming sessions, with their many permutations, makes manual tracking infeasible. AI-based anomaly detection solutions monitor operating systems, game levels, user segments, and devices to ensure that bugs and flaws affecting user experience are quickly identified and fixed. Outfit7, for instance, uses anomaly detection to predict and manage issues as their games evolve.
Technical Implementation: Anomaly detection in gaming often involves analyzing data related to game performance, user interactions, and system metrics across different devices and operating systems. Machine learning models are trained on historical data from gaming sessions to learn the patterns and trends associated with optimal gameplay. These models can then continuously monitor real-time data, detecting any anomalies that could indicate bugs or other issues. Once detected, developers can quickly address these issues to ensure a seamless gaming experience.
Identifying inefficient equipment and tools in manufacturing
Anomaly detection in manufacturing involves using machine learning and data analytics to identify unusual patterns or deviations in the performance of equipment and tools. By monitoring data from sensors, logs, and other sources in real-time, manufacturers can use anomaly detection algorithms to pinpoint unproductive equipment and tools. This enables timely intervention to improve efficiency and reduce downtime.
To implement anomaly detection in manufacturing, data is first collected from equipment and tools using sensors, logs, and other sources. This data includes metrics like temperature, vibration, pressure, and energy consumption. The collected data is then stored in a centralized database for analysis.
Before analyzing the data, it is preprocessed to remove noise, outliers, and other discrepancies. This preprocessing helps improve the accuracy and effectiveness of the anomaly detection algorithms. Relevant features or attributes are extracted from the preprocessed data, which are used to characterize the performance and behavior of the equipment and tools.
Machine learning models are then trained on historical data to learn the patterns and relationships between the features and the normal behavior of the equipment and tools. The choice of supervised, unsupervised, or semi-supervised machine learning techniques depends on the availability of labeled data.
Once the models are trained, they continuously monitor the real-time data from the equipment and tools to identify deviations from the established patterns. Anomalies may include sudden changes in temperature, vibration, or energy consumption that could indicate unproductive or inefficient operation.
The system generates alerts for the maintenance or operations team when an anomaly is detected. The system may also provide insights into the root cause of the anomaly, allowing for timely intervention and corrective actions. Anomaly detection can also be used in conjunction with predictive maintenance techniques to estimate when equipment or tools may become unproductive or fail in the future. This helps plan maintenance activities to minimize downtime and optimize production schedules.
The outcomes of the interventions are fed back into the system to continuously improve the anomaly detection model, making it more accurate and robust over time. Anomaly detection is a valuable tool for manufacturers to locate unproductive equipment and tools, improve efficiency, reduce downtime, and optimize production processes.
Mitigating risks and enhancing security in IT and telecom
In the fields of Information Technology (IT) and telecommunications, anomaly detection plays a crucial role in identifying and addressing various challenges and threats, such as user privacy concerns, financial risks to providers, and other unexpected hazards. Organizations can uncover irregularities or abnormal patterns that deviate from established baselines by employing machine learning and statistical analysis techniques to monitor network traffic, server logs, call records, and other relevant data. These deviations may indicate potential threats or issues.
For example, in the case of user privacy concerns, anomaly detection can help identify unauthorized access to sensitive information or unusual data usage patterns, which could indicate a data breach or other security incident. By proactively detecting these anomalies, organizations can respond more quickly to mitigate the impact and protect user privacy.
In terms of financial threats to providers, anomaly detection can be used to monitor billing data, transaction records, and other financial information for signs of fraud or abuse. By detecting unusual spikes in usage, unexplained charges, or other irregularities, organizations can more effectively protect against financial losses and ensure the integrity of their billing and accounting systems.
In the broader context of IT and telecom, anomaly detection can also be used to identify technical issues, such as network congestion, server outages, or hardware failures, that may disrupt service or impact overall system performance. Organizations can quickly diagnose and resolve issues by detecting these anomalies in real-time, minimizing downtime and improving overall system reliability.
How LeewayHertz’s generative AI platform helps in anomaly detection in diverse business environments?
LeewayHertz’s generative AI platform, ZBrain, plays a transformative role in optimizing various facets of anomaly detection. As a comprehensive, enterprise-ready platform, ZBrain empowers businesses to design and implement applications tailored to their specific operational requirements. The platform uses clients’ data, whether in the form of text, images, or documents, to train advanced LLMs like GPT-4, Vicuna, Llama 2, or GPT-NeoX for developing contextually aware applications capable of performing diverse tasks.
Anomaly detection is crucial for business operations as it helps identify unusual patterns or irregularities that could signal potential issues, such as fraud, operational inefficiencies, or system failures. By detecting these anomalies early, businesses can proactively address problems, ensuring smoother operations and maintaining high standards of quality and security.
ZBrain effectively addresses challenges associated with anomaly detection through its distinctive feature called “Flow,” which provides an intuitive interface that allows users to create intricate business logic for their apps without the need for coding. Flow’s easy-to-use drag-and-drop interface enables the seamless integration of large language models, prompt templates, and media models into your app’s logic for its easy conceptualization, creation, or modification.
To comprehensively understand how ZBrain Flow works, explore this resource that outlines a range of industry-specific Flow processes. This compilation highlights ZBrain’s adaptability and resilience, showcasing how the platform effectively meets the diverse needs of various industries, ensuring enterprises stay ahead in today’s rapidly evolving business landscape.
ZBrain apps enable precise anomaly detection, which contributes to more accurate and effective risk management strategies. This increased efficiency and accuracy in identifying and addressing anomalies not only ensure smoother operational workflows but also bolster the overall security and integrity of business processes.
Endnote
Artificial intelligence has changed how we approach anomaly detection across various industries, proving to be an invaluable tool for identifying irregular patterns and potential risks. AI-powered anomaly detection techniques have enhanced the speed, accuracy, and efficiency of monitoring vast amounts of data, enabling organizations to respond proactively to potential issues. From preventing fraudulent activities in retail and financial sectors to improving patient outcomes in healthcare and optimizing manufacturing processes, AI has become a key player in making operations more secure, efficient, and reliable. The ability of AI to analyze and learn from data in real-time empowers organizations to anticipate problems before they occur, providing a competitive edge and enhancing customer satisfaction. As technology advances, AI’s role in anomaly detection will undoubtedly become even more integral, further solidifying its importance in shaping a smarter, more responsive future.
Protect your business from unforeseen risks. Contact LeewayHertz AI experts to build a robust, leak-proof anomaly detection system and ensure the safety and efficiency of your operations.
Start a conversation by filling the form
All information will be kept confidential.
Insights
From legacy systems to AI-powered future: Building enterprise AI solution for insurance
Building enterprise AI solutions for insurance offers numerous benefits, transforming various aspects of operations and enhancing overall efficiency, effectiveness, and customer experience.
AI in sales: Transforming customer engagement and conversion
AI offers substantial assistance at various stages of the sales process, changing the way sales teams operate and enhancing overall efficiency.
Topic modeling in NLP: Extracting key themes/topics from textual data for enhanced insights
Topic modeling is a popular technique used in natural language processing and text mining to uncover latent themes and structures within a collection of documents.